IT Security DDOS Attacks

What are DoS / DDoS attacks?
DoS (Denial of Service) Attacks
The common Dos attack is where hackers use a relatively powerful single computer to attack a target IP, this is a one-to-one attack (DDoS is a many-to-one attack). DoS sends a large number of meaningless network messages to the target IP in the form of message flooding, exhausting system or network resources and making the service unable to operate normally.
DDoS (Distributed Denial of Service) Attacks
DDoS has evolved from DoS. DDoS attacks allow hackers to take control of multiple malwareinfected computers or other devices such as IoT devices, this is becoming what is often heard as a “zombie computer”. As the source of attack traffic, these zombie computers launch a “denial of service” attack on a specific target IP, introducing a large amount of network traffic, overwhelming the server or network, causing the host to temporarily interrupt or stop the service.
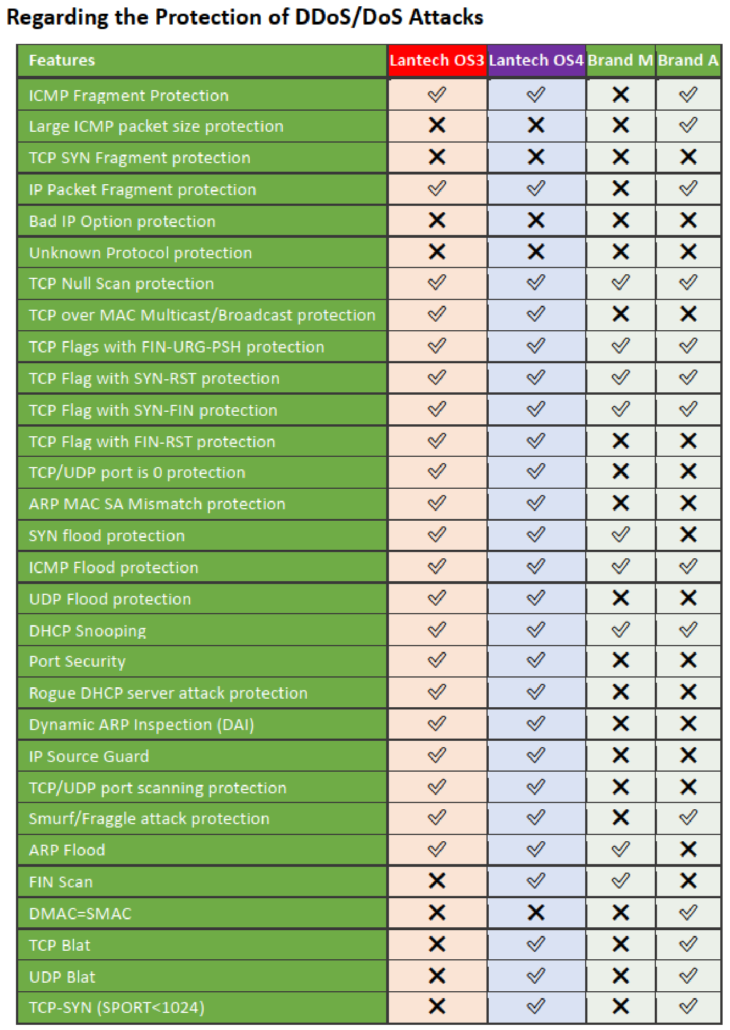
Lantech solutions to prevent DoS / DDoS attacks
DoS (Denial of Service) Attacks
The common Dos attack is where hackers use a relatively powerful single computer to attack a target IP, this is a one-to-one attack (DDoS is a many-to-one attack). DoS sends a large number of meaningless network messages to the target IP in the form of message flooding, exhausting system or network resources and making the service unable to operate normally.
DDoS (Distributed Denial of Service) Attacks
DDoS has evolved from DoS. DDoS attacks allow hackers to take control of multiple malwareinfected computers or other devices such as IoT devices, this is becoming what is often heard as a “zombie computer”. As the source of attack traffic, these zombie computers launch a “denial of service” attack on a specific target IP, introducing a large amount of network traffic, overwhelming the server or network, causing the host to temporarily interrupt or stop the service.